Singapore-based cyber-security company Group-IB explains today in a study major changes reported since the second half of 2018 and the first half of 2019 on the continuum of high-tech threats.
RedCurl, a new opponent
In 2019 attacks against insurance, consulting, mining, ironworks, retail and construction companies for spying and financial theft were detected by a new group called RedCurl. Group IB says this threat actor is highly capable and hard to detect. The use of legal networks to connect with its command and control servers (C2) allows RedCurl to fly under the radar. The actor of the attack relies on a custom Trojan for his malicious acts and concentrates first on stealing the victim’s valuable documents and then installs Monero cryptocurrency XMRIG miners on the infrastructure. RedCurl seems to be involved in negotiations and information concerning fees and deals for the data stolen from survivors. The high quality of their phishing attacks is a special feature of this opponent. We tailor the messages for each person we seek, ensuring a higher rate of success. It is currently unclear if RedCurl is a cyber-criminal or a state-sponsored organization. Nevertheless, Group-IB seeks to determine its membership by looking at resources, strategies and procedures. Most of the victims in Eastern Europe are in North America, with a compromised organization. Judging by the language in the decoy documents and the services used to set up an e-mail server, the group at least speaks Russian, Group IB told us.
Money-driven assailants
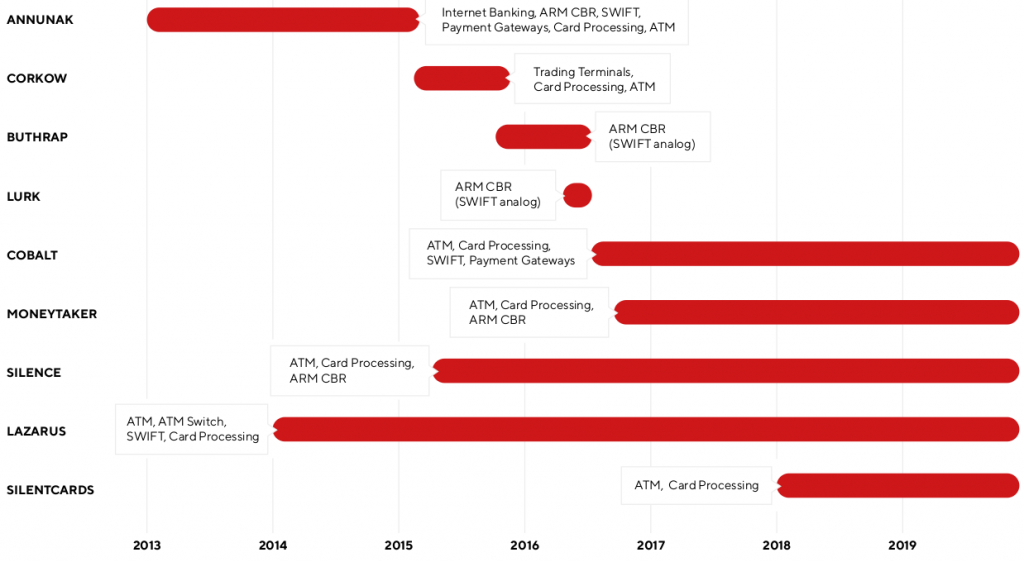
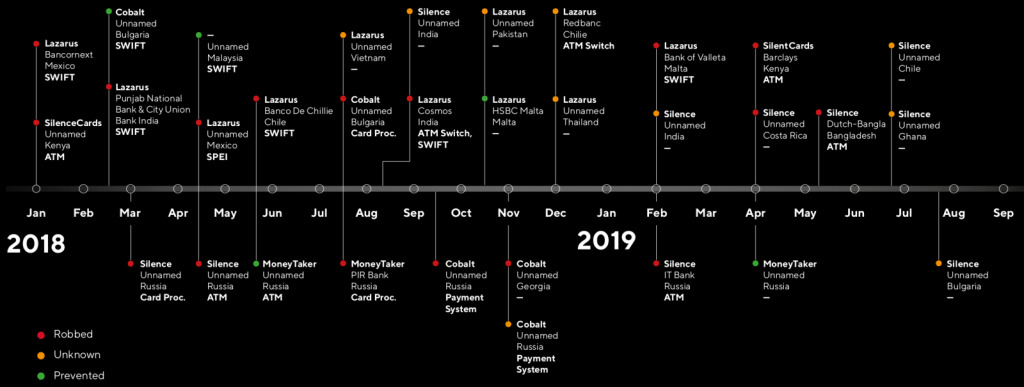
The Group IB names five cybercrime outfits active in attacking financial institutions, three of which are Russian speakers (Cobalt, Silence, MoneyTaker) and the only ones working with trojans who control cash at will by ATMs. The other two are Lazarus and SilentCard, a new Kenyan group targeted at and competitive in Africa, despite having fewer technical skills than the other players in the same business.
Although the financial sector is affected by other actors, the Group-IB study considers the five to cause severe damage. Such teams usually take a long time to learn the ropes in the compromised network so that they can manage both financial operations and the workers they supervise. A successful and failed map of the attacks shows that they have been busy since the second half of 2018, almost every month trying their luck.
Information of SilentCard are currently scarce; however, the researchers concluded that the team worked locally and engaged in two successful projects. Only a malware sample is available, and Group-IB assumes that SilentCard uses “a controlled device within the organization to attack the company network.”
State-backed actors
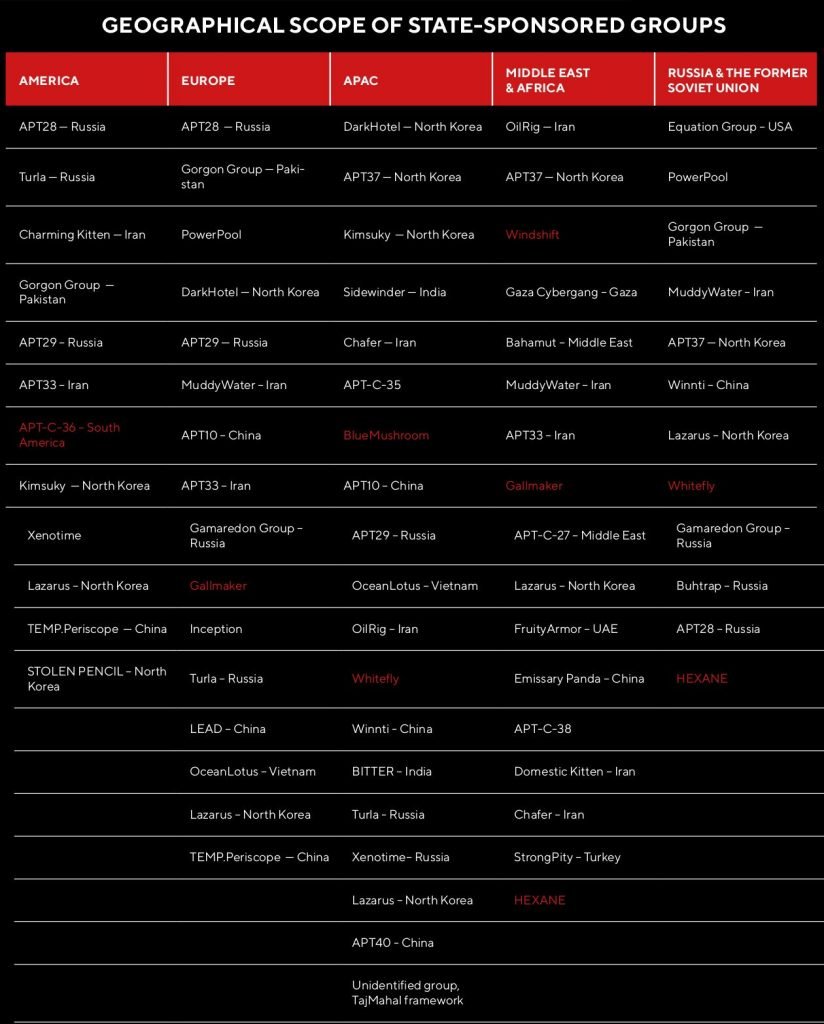
Attackers working for a government, also known as APT groups, were also active, with 38 groups active throughout the group-IB period. Of these, seven were found to conduct cyberespionage operations this year. Although the new groups were only identified last year, they existed for longer, some as early as 2011.
One is Windshift, the instruments and tactics of which DarkMatter analyzed in August 2018. However, since 2017, it has been in the cyber-espionage game aimed at government employees and critical infrastructure facilities in the Middle East. Blue Mushroom (also referred to as Sapphire Mushroom and APT-C-12) has been active since 2011 but only in mid-2018 it appeared on the radar. According to a Qihoo360 article, its priorities are in the nuclear industry and scientific research. Gallmaker is another APT unit that was discovered in 2018 but has been active since at least December 2017. It relies on live-off – the-country instruments to attack government and military targets. Research published earlier this year by Qiho360 exposed the activities of the South American APT-C-36or Blind Eagle threat group which has been active in stealing trade secrets from key companies and government agencies. Whitefly primarily targets education, news, telecommunications and technology companies in Singapore. Its activity was tracked back to 2017 even though in July 2018 it was attacked by the largest public health organization in Singapore; 1.5 million patient records were stolen. Hexane or Lyceum is involved in vital Middle East infrastructure and was first publicly disclosed in August, although its activities were under investigation well before that date. SecureWorks has released its modus operandi with technical details. The seventh APT party remains unknown as the attacking system it uses is little talked about. Kaspersky, called TajMahal, found that the kit had approximately 80 modules and was used to compromise a diplomatic entity in Central Asia.
The proliferation of cyberwar
For political leaders, cybersecurity has become a common theme and a pillar of military operations. Attacks mentioned in public documents indicate that they lose their covertness gradually. Governments that use digital tools to counter adversary operations are not a guess but a real thing any more. Many energy plants have been affected by cyber attacks and hackers have no financial gain. Retaliated cyber-attack enemies, the main one over the summer, was U.S. action against Iran’s weapon system to shoot down a U.S. surveillance drone and attacks on oil tankers. Dmitry Volkov, Group-IB CTO and head of Threat Intelligence said that the 2018 cyberworld was unprepared for side-channel attacks and microprocessor vulnerabilities, while covert military activities in cyberspace in 2019 are exposed. “Groups acting in the national interest fly under the radar for many years. Only a few such incidents have become known but most indicate that the critical infrastructure of many countries has already been compromised” – Dmitry Volkov