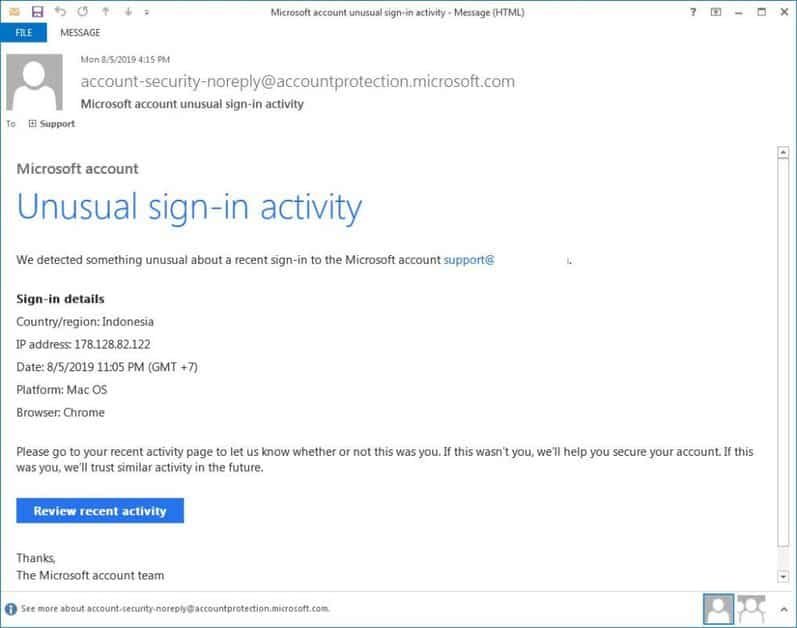
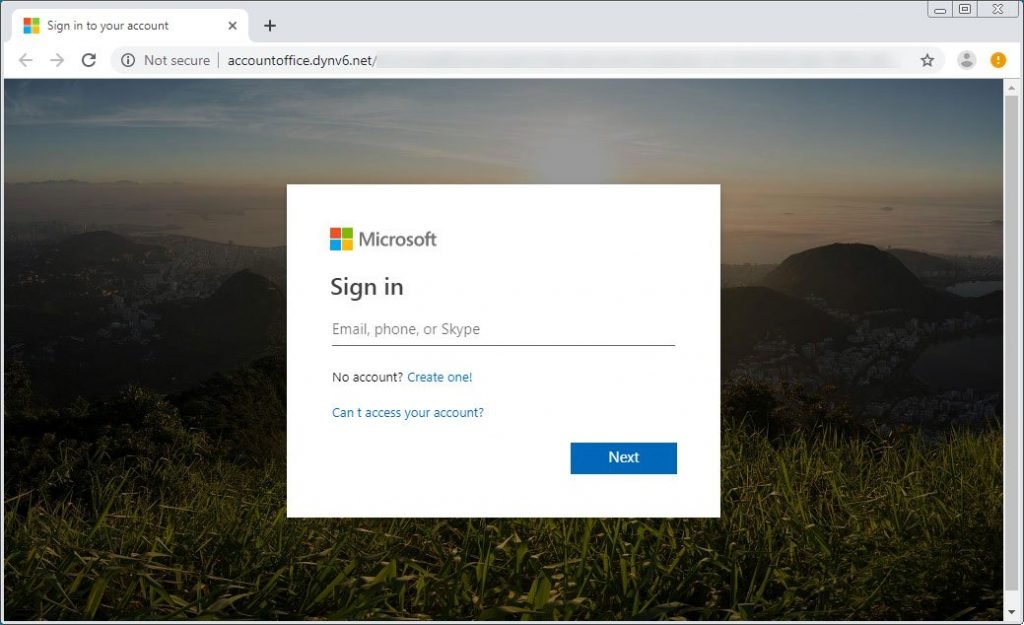
With businesses like Google and Microsoft, which frequently send users alerts when they discover abnormal activity on their account, customers may feel normal to receive them and then click on the links below. Attackers capitalize on this by emailing Microsoft’s “Microsoft Account Unusual Login Activity” alerts. Compared to Microsoft’s legit email notifications, they almost look like the same data areas and even the same “account-security-noreply@accountprotection.microsoft.com” sender address. Microsoft account unusual sign-in activity email What is distinct, however, is that if you click the “Review Recent Activity” email connection, you are carried to a fake landing page at a non-Microsoft site which asks you to login instead of going to Microsoft to review the activity for your account.
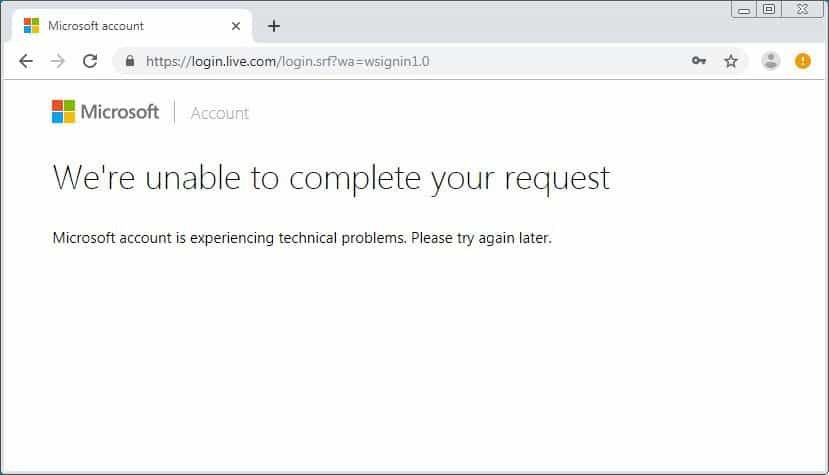
Fake Microsoft Account Login. If a victim enters his credentials, the information will be saved so that the phishers can access your account later. Regardless of which credentials are in the wrong type, the user is always forwarded to an error section on the live.com site of Microsoft. This is to make it look like your account has a issue and nothing foreign happens. Login Failed Although some users may feel that the e-mails are safe because they have a legitimate Microsoft e-mail address, it is always important to remember that an e-mail from any account that an attacker wants can always be spoofed. Therefore, even if a phishing e-mail appears to be valid, you must keep in mind the URLs in the landing pages before entering your login credentials in the login form displayed.