A cybercrime group, known mainly to hack retailers and steal payment card information from point – of – sale (POS) systems, has changed its tactics and is now also deployed on infected networks. The group, FIN6, is reputed to be one of the most advanced cybercriminals in the field of cybersecurity. The activities of FireEye were initially documented in spring 2016 when a first report was published detailing the extensive hacking and advanced arsenal. The group developed a multi-faceted POS malware strain called Trinity (a FrameworkPOS). FIN6 would hack in major retailer networks, move over their systems laterally and deploy Trinity on computers that handle POS data so that it could extract payment card information, which it would then upload on its own servers.
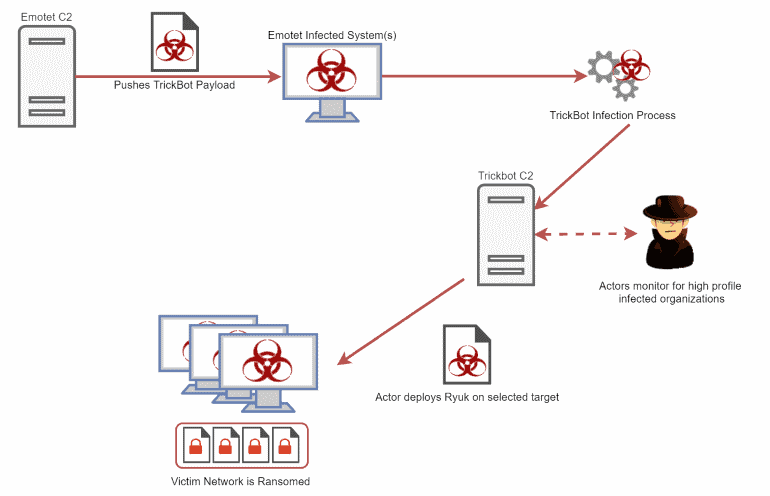
— Catalin Cimpanu (@campuscodi) 28 March 2019 By selling these stolen card details on the forum, the group would make money and raise millions of US dollars. Fin: RANSOMWARE DEPLOYING SINCE JULY 2018 However, according to a new report published by FireEye on Friday, 5 April, the group is now deploying POS – not – managing ransomware on some hacked networks. And the group did not drop just ransomware of any kind. The group has been deploying Ryuk and LockerGoga ransomware strains since July 2018, says FireEye. Both of these strains were at the heart of a high – profile infection wave that crippled both governmental organizations and large private sector companies – Norsk Hydro being the latest victim. The group is believed to be operating from Russia, where it rents infrastructures to large companies (Emote, and TrickBot), that it would eventually infect Trinity, Ryuk or LockerGoga, according to previous reports from Crowd Strike, FireEye, Kryptos Logic, McAfee, IBM and Cybereason.
Image:Kryptos Logic IS FIN6 Now The First RANSOMWARE GROUP? In its latest FIN6 report, FireEye found this change in tactics from Trinity to Ryuk / LockerGoga. However, analysts of the company could not be sure if this is the main modus operandi of this group now, or if this is just a side activity carried out by some group members “independent of the Group’s payment card violations.” But whether or not FIN6 is now the first ransomware group, companies and their departments of cybersecurity need to be carefully aware of this new development, read the recital.
— PaulM (@pmelson) 5 April 2019