I’ve only listed apps that work. I hope these apps are going to please you. I have divided these applications into two categories: Apps for hacking learning (1-4), and Hack tools for android (5-16).
Best Android User Hacking Apps
This app gives you the opportunity to learn how to use Kali Linux tools. It isn’t for young people but if you know anything about Kali Linux or about Kali Linux already installed, you can use it for knowing how to use Kali Linux.
Download You know how many Linux commands a hacker can use. Nearly every hacker uses a Linux operating system. Linux commands are very important in the hacking process.
Download You will learn about SQL Injection, cross-sectional scripting, file include etc. and watch this video in order to find out more. Get to know about free online sql injection scanner here.
Download Use this application to learn Metasploit when you begin using Kali Linux or any Linux distribution for Hacking. This app I’m not going to recommend to beginners.
The above apps are therefore useful to learn hacking, but these apps are used to hack. I’ve been reading many articles on Android hacking apps. Most of the items are obsolete. No update of their articles was done by bloggers. Today’s apps such as Faceniff won’t work. All these apps work today, I don’t know what the future will be. Download If you’re just beginning perhaps you do not like this program. But if you understand something about hacking afterward you are going to find it rather helpful. Everything you can do Using zanti
Scan the Entire system show living host scan interface via Nmap Scan support running on every interface Find exposure Perform Brute force attack Perform Shellshock Man In The Middle Attack Session Hijacking SSL Striping (it Isn’t working anymore since google mend all difficulties in their newest upgrade ) Sniffing packets Replace picture Redirect URL and IP
Download This is my favorite program for Hacking. It is magnificent. Using this it’s possible to set up many hacking programs in an Android smartphone such as Metasploit, Nmap etc.. Using this you may learn Linux controls. It’s offered in play shop and it functions without origin. You require a good deal of patience if you’re a newcomer since this isn’t beginners to Hacking. That is why I connect Linux commands program for users Getting beginning with Termux The best way to install a bundle on termux To set up Metasploit Metasploit in activity The best way to set up Nmap Nmap tutorial for novices
In beginning since you’re just beginning, you will need patience. If you want my help allow me to know by opinions Download It is a network scan tool, as its name shows. This tool allows you to scan your wireless network. It scans the entire network and detects the IP address of all connected devices. This app also allows you to find network speed. You can analyze the device in advance by using NetBIOS, the UPnP etc…, the application is rated 4.5 by 2,93,335 users which shows how incredible this app is. You can then analyze it using NetBIOS, UPnP etc. Download This is not an application for hacking. It can be used to gather information such as IP address, traceroute etc. I don’t like this application, personally. But you can try that if you know SQL injection, you can use Google dorks present in this application to find a SQL vulnerable website. But will you manually use a mobile phone to hack an SQL injection site? Sound odd! Download This app is great to install netHunter on a single Android smartphone. You need to root your phone. Use tools like mac change machines, nmap, custom commands and more. Download This is a non-official Android user version of Nmap. Things like os scanning etc. cannot progress. This app is available in the GPS shop. Network mapper: android hacking app Overall, I found the best app is zanti scanning.
Download For people familiar with SQL injection, a time-saving app can be app, tables, etc. are automatically found. All SQL injection can be done with DroidSqli based upon time, blindness, error and normal. Download You know how many encryption and decryption. This application can be used to encrypt and decrypt data. In hacking, you sometimes need to provide data by encryption in bases16, 32, etc. If you are well aware of encryption, you can use this instrument. It also encrypts and decrypts data. It does both things. The app is free as well as pro version. Some of the pro version and free version encryption algorithms contain ads. Base : – Base16 – Base32 – Base64 – Base85 (PRO VERSION) – Base91(PRO VERSION) Conversion : – Hex – Decimal – Binary – Octal (PRO VERSION) Cipher : – Atbash – Caesar – ROT13 – Vigenere – Affine – Rail Fence – Scytale – Beaufort (PRO VERSION) – Baconian (PRO VERSION) Hash : – MD2 – MD5 – SHA-1 – SHA-3 – SHA-224 – SHA-256 – SHA-384 – SHA-512 (PRO VERSION) – Keccak (PRO VERSION) String Tools : – URL Encode – HTML Entities – Reverse Download With this app, you can wps to wifi. WPS is vulnerable to security. A pin may be used for password purposes. These default pins are only used in this app. Wireless internet is mostly hacked. This app also allows you to use brute force attack. Download You can access any computer with ssh remotely. To connect your server, people use it. The authentication is password less. Android phones can also be connected via ssh. It’s not an app to hack. If you have SSHDroid installed you can connect the phone on your network
Download How awesome if you can use an android device to create a bootable USB drive. But probably you’re thinking about how we can hack. Let me tell you that you can use LIVE LINUX to prevent you from installing it. You can therefore use it and browse files or open the application by password. But you don’t need to split the password, without the password, you can get full access. You may even install Linux using it before using it, I recommend you view this video. Enter a quick internet link because the image file needs to be downloaded from the Internet. Download How many use tor on your computer to hide. Basically, if you browse Tor, there is nobody who can find your actual location. There are illegal deals, such as the sale of drugs. Now you can use your Android phone for this network too. The app has 10,000,000 and more users installed, and has a 4.5 rating for 141,870 users. Download These apps are suitable for monitoring android devices. Such as WhatsApp SMS collection records, etc. This is a full list of the best spy applications. Try these apps if you wish to hack your girlfriend’s phone. These apps capture each keyword typed on your phone and send it back to you remotely This is the best keylogger I’ve found. It is paid but can be used for 3 days in a free trial. Don’t worry that the credit card isn’t being requested. All log files such as SMS, Call Database and keystrokes will be sent remotely. While all keystrokes can be recorded, all app data are separated. After 5 minutes it will send log files. The Time interval for sending log files may be set. How to Setup/Install?
- Visit and click on Free Download Trial
All log files such as SMS, call record and keystrokes will be sent to you remotely. Although all keystrokes are recorded, all application data are separated. After 5 minutes, it will send log files. The time interval for sending log files can be specified. 2. Check your email account after registration. You are going to get a mail like this from ikeymonitor. 3. Open and connect to your account with ikeymonitor. You’ll see this popup when you log in
I’m using Android and I’m going to pick Android. Choose from the first two options on the Confirm page. The first option, I’ll choose.
Afterwards, an app download link will be displayed.
Download this to the victim phone and install it. Installation is very easy It will require your license key in your mailbox. In any case, you can’t log in and then use the link for assistance
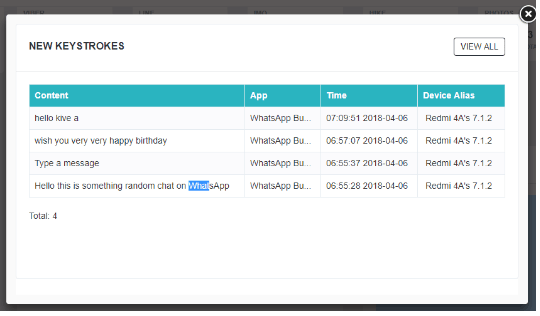
You can get logs online after successful installation. I just open up my WhatsApp and here are results in random words. It will send you important records online, as you see. Simply install once and forget it. Apps that send log files remotely, also free keylogger applications. I’ll prefer ikeymonitor between hoverwatch and ikeymonitor. Due to the free version, floverwatch features are limited while ikeymonitor features all free trial features. Download The Spy app is ikeymonitor-like. If you can spend money, try that because it’s cheaper in the long run than the ikeymonitor. The installation process is almost ikeymonitor-like. Download These spy applications are expensive. Okay! I therefore have for you a simple solution. How can you record in the background your device display?
You can use it as a spy app, but not send videos you have captured online. Only on your phone can you use it. There are a lot of apps like that, but I found it to be better than others. Password and this application can be used. Download I told them those hacking apps that are no longer working I had read many blogs before this article was published and I found that some bloggers have listed many obsolete apps that don’t waste your time on those apps. FaceNiff: I hate this entirely. You could hack Facebook accounts etc because I’ve read it everywhere. A Google guy is going to step forward. These bugs have been fixed a long time ago. All right, let me explain. All right. If your network is connected, all HTTP information (like the user’s password) of any devices connected to this network can be viewed. We mainly have https in this browser to encrypt data in order to handle the problem. This means secure. Hacker couldn’t read it, then. For every computer, he needs a key which is different. However, some find a way to circumvent https to view all network data. To this end, FaceNiff is used. This issue has now been solved by Google. Androrat: First of all, the download link to this application is not found and it will be time-consuming. I’m not using it works for any device or because it has been created and not updated many years ago. Basically, this is a spy application. The above-mentioned spying apps are available. Don’t try one WiFi kill: essentially this is a jammer wireless app. It claims that it stops wireless Internet access on other devices. To use this app, you must root your phone. I tested that. I tested it. I tested two rooted devices, but no outcome. Perhaps this is an adequate wifi network. In any case, it didn’t work. I hope you enjoy these apps in conclusion. Let me know by comments if you have any trouble. I’m going to help you glad.