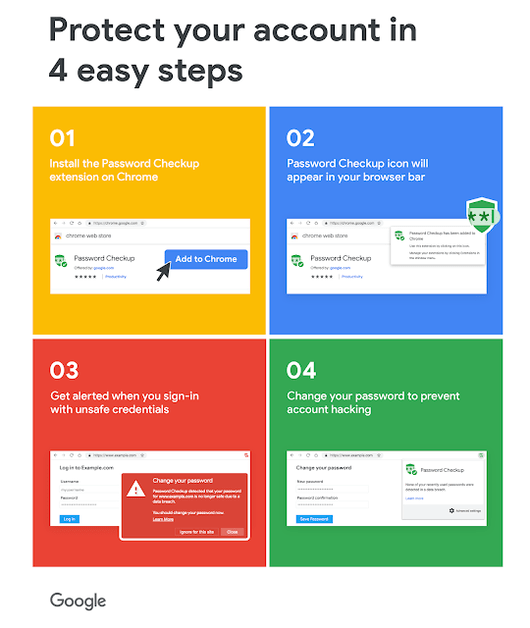
Today, on Safer Internet Day, Google released a new Chrome extension called “Password Checkup, “which checks whether usernames and password combinations entered in login forms were leaked online during past data breaches and security. The extension works on an online service every time users log on. The extension takes the username and password entered in the login form and checks it against a database of more than four billion credentials collected in recent years by Google engineers from public breaches. If the username and password combo is found in Google’s internal database of unsafe credentials, the extension will display a pop-up alerting the user that the credentials must be changed.
Google said that the extension was designed with privacy in mind, so that both Google and the attackers cannot abuse it to reveal or learn passwords from the user. “Together with cryptography experts at Stanford University, Password Checkup was designed to ensure that Google never learns your username or password and that any breach data is safe from wider exposure, “said Google today. The extension works very much like the Firefox Monitor service that Mozilla shipped in November 2018 with Firefox. But the two services are very different under the hood. Firefox Monitor works by displaying a one-time alert when users navigate to a website that was broken in the last 12 months and politely requests users to consider changing passwords. Google’s new Password Checkup extensions, on the other hand, work more proactively to check actual login usernames and passwords. Firefox Monitor also works on the Have I Been Pwned service, while Password Check works with an internal Google database of leaked credentials other than Have I Been Pwned. According to Google, the extension does not check single usernames and passwords, but both items simultaneously, as a combo. This means that the extension will not display alerts when users use simple passwords like “123456, “but only when both the username and the password are found in previously leaked data together as a combo. Google said the reason why it doesn’t alert users when they use simple or previously leaked passwords is because they tried to avoid an alert / popup fatigue that might have led users to completely ignore the alerts. The reason for the creation of this extension is that threat groups use old leaks ‘ username and password combos to launch credential stuffing attacks, trying to access other online accounts where users have reused their old username and password combos. These types of attacks have recently intensified, with DailyMotion, Reddit, Basecamp, HSBC, Dunkin ‘ Donuts, AdGuard and similar incidents reporting. Google has also seen these attacks, reporting that attacks on nearly 110 million users have been blocked in the past with the same four billion leaked credentials database that the Password Checkup tool is now using. “We want to help you stay safe not only in Google, but also on the web elsewhere, “said Google today.” Since this is the first version, we will continue to refine it over the coming months, including improving site compatibility and username and password field detection. “Please refer to the official Google announcement for details on the cryptography that the extension uses to save usernames and passwords entered in login forms from both Google and third-party attackers. You can download the Password check-up extension from the official Chrome Web Store here.