The malware was first discovered in November last year, and has been deployed across Europe in attacks against diplomatic institutions. Responsible for the attacks is a organization known as Turla, a Russian threat actor funded by the State who has previously engaged in cyber-espionage operations. Turla has a long history of using innovative, non-standard methods to build malware and perform stealthy attacks. The group was known to hijack and use telecommunications satellites to deliver malware to remote parts of the globe, developed malware that hid its control mechanism inside comments posted on Britney Spears’ Instagram photos, developed email server backdoors that received commands via spam-looking messages, hacked cyber-espionage hacker groups from other countries and modified them. Kaspersky has disclosed another of Turla’s innovative strategies in a study published today — namely malware that receives instructions from command and control (C&C) servers in the form of HTTP status codes.
Latest Edition of COMpfun
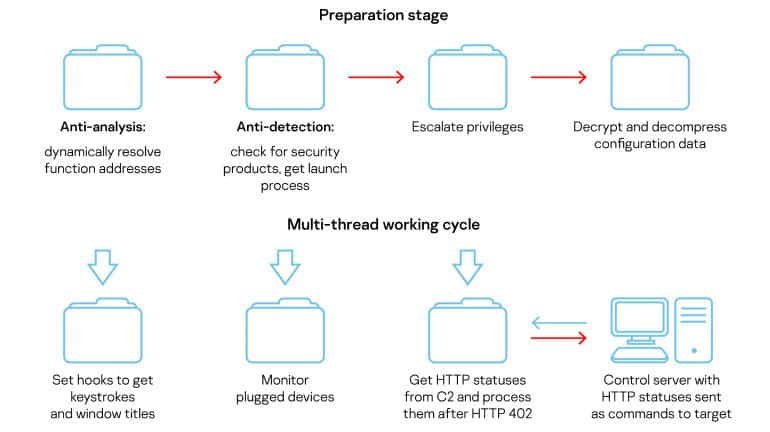
This specific malware is called COMpfun, and is a classic Trojan remote access (RAT) that infects victims and then collects device data, logs keystrokes, and takes user desktop screenshots. Any data collected is exfiltrated to a remote C&C server. In 2014 the first version of COMpfun was seen in the wild, and detailed here in a G DATA report. Kaspersky claims they spotted a new edition of COMpfun last year, today.
This latest updated edition was different from older versions of COMpfun. In addition to the classic data collection features similar to RAT, Kaspersky says the new COMpfun version also included two new additions. The first was their ability to monitor when removable USB devices are connected to an infected host and then propagate to the new device itself. It is thought that the feature is a self-spreading mechanism used by the Turla group to infect other systems on internal and/or air-gapped networks.
New code-based C&C protocol with the HTTP status
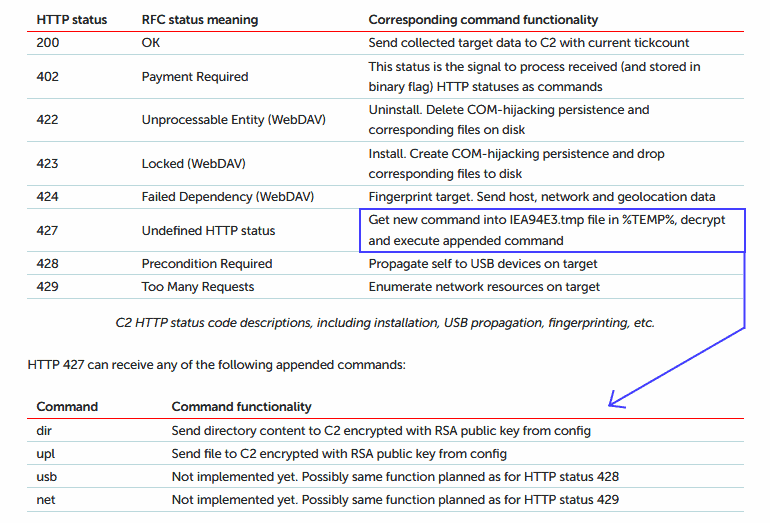
The second addition is a new communications system with C&C. This new C&C malware protocol does not use a classic pattern where commands are sent directly to the infected hosts (the COMpfun malware implants) as HTTP or HTTPS requests carrying clearly defined commands, according to Kaspersky. HTTP / HTTPS traffic is also checked by security researchers and security devices for patterns that look like malware commands. When they see CLI-like parameters in headers or traffic over HTTP, it is generally an obvious sign that something suspicious is happening. The Turla group developed a new server-client C&C protocol that relies on HTTP status codes to avoid this kind of detection. The HTTP status codes are globally standardized responses given to a communicating client by a server. The status codes contain a server state, and they’re used to tell the client (usually browsers) what to do next — including dropping the connection, supplying passwords, refreshing the connection, etc. Kaspersky says Turla has adapted this simple server-client process that has been around for decades to COMpfun’s C&C protocol, where the COMpfun C&C plays a server role, and the COMpfun implants running on infected hosts play a client role. Kaspersky says that all subsequent status codes are future commands each time a COMpfun implant pings the C&C server if the server responds with a 402 (Payment Required) status code. For example, if the COMpfun server responded with a 402 status code, followed by a 200 status code, the malware implant would upload all the data it collected to the Turla C&C server from a host ‘s computer. Researchers say the following HTTP status codes and their associated COMpfun commands have been able to reverse engineer them.
Once again the COMpfun study reveals why Turla is considered one of today’s most advanced cyber-espionage groups. The group has invested heavily in stealth with a history of attacking diplomatic targets, something which not many Russian state-hacker groups have done, most of which are very loud in their operations. Additional details regarding the COMpfun malware and compromise indicators can be found in the Kaspersky report.