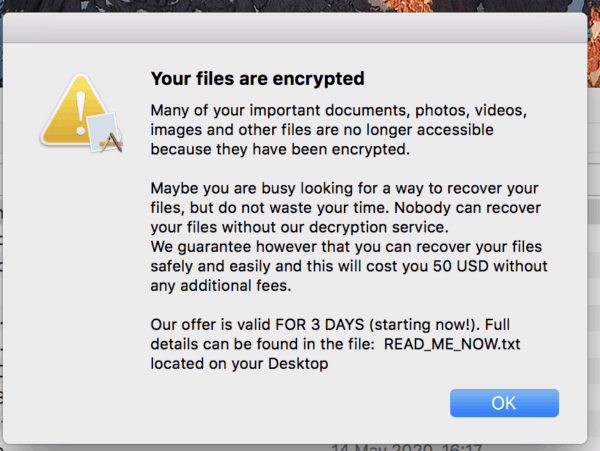
ThiefQuest, initially called EvilQuest, is designed to encrypt files on compromised systems but also enables its operators to log keystrokes, steal files and take full control of the infected device. ThiefQuest was originally classified as ransomware, but a closer examination found that criminals couldn’t figure out the victims paid the ransom, the led researchers to conclude the ransomware features were intended to mask the activities of data theft. ThiefQuest is supplied to macOS applications such as the Ableton and Mixed in Main DJ apps and the Little Snitch firewall as trojanized installer. When the malware is enabled, it begins encrypting files that are located on the computer, after which it tells victims that their files have been encrypted through text files and a modal window, and that a $50 ransom has to be paid in bitcoin to recover them.
However, as Bleeping Computer points out, all victims are given the same bitcoin address and there’s no way for the victims to get in contact with the attackers to let them know the ransom has been charged. In addition, Apple security expert Patrick Wardle found that the routine for decryption is not called anywhere in the malware code, suggesting that it never gets executed. Malwarebytes researchers found out that the malware will not always encrypt data, even though it appears to have done so, which further means that the capabilities of ransomware are only a diversion. SentinelOne has provided a free decryption service for Mac users whose files had been compromised by the malware. Researchers at the company studied ThiefQuest and found that its author had left the role of decryption in the malware code. When they were able to retrieve the key required to decrypt the files, they used the decryption function proper to the malware to restore encrypted data. ThiefQuest is designed to steal, from infected systems, documents , images, source code, databases, encryption keys and cryptocurrency wallets. Wardle’s threat analysis revealed it’s also looking for executable files and adding malicious code to those files. This would allow it to spread like a virus that is extremely uncommon for malware on Mac. “The fact is that most (all?) recent examples of macOS malware are not computer viruses (by the conventional definition), since they don’t attempt to reproduce themselves locally. But OSX.EvilQuest does …make it a real machine virus for macOS!! “Said Wardle.